Checking your password against data breaches
Marc Burrows
Senior Software Engineer, Βι¶ΉΤΌΕΔ Account
Tagged with:
In the Βι¶ΉΤΌΕΔ Account team, we’re constantly trying to find better ways to keep your account data safe. Part of this includes making sure you choose a secure password.
When Βι¶ΉΤΌΕΔ Account was launched in 2015, we followed the OWASP authentication guidelines on password security. It suggested:
- a minimum of 8 characters
- a mixture of letters, numbers or symbols
- not matching the first part of your email address.
These guidelines were a good starting point. But over time, more security insights have become available.
A new password checker
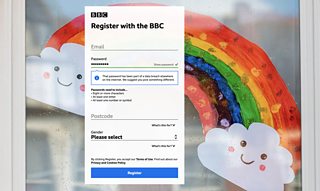
We’ve just released a new feature for when users register for a Βι¶ΉΤΌΕΔ account, or reset their password. This checks the chosen password against a large list of passwords previously exposed in data breaches elsewhere on the internet, which are in the public domain. We can then recommend changing the entered password.
The feature came about as a prototype in 2019, with two software engineers working together during ‘10% time’: a day every two weeks where the engineering team works on ideas to improve our engineering processes, come up with new features, and create quick proof of concepts.
The password checker uses a service called , created by web security expert Troy Hunt.
Why do we check passwords?
We’ve put together this password checker so you know if your password isn’t as safe as you might think. It means you can choose a different password on the Βι¶ΉΤΌΕΔ – and importantly, stop using it on other websites and services too.
The most common way in which hackers access an individual’s accounts is by assuming users reuse the same password across their accounts. If you use the same password for every website, or even a similar password with a different ending, then your information is only as safe as the least secure of those websites.
Does this mean you’re sharing my password with someone?
No, and we will never do so. The process of how this works can be seen in the diagram below, with further explanation afterwards.
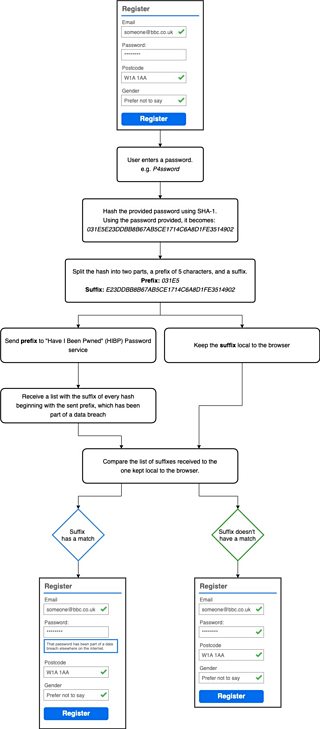
1. You enter a new password on the registration or forgotten password form
2. We take this entered password and hash it using the SHA-1 cryptographic hash function (To find out more about why we use this, please read about the service)
3. Of this created hash, we extract the first 5 characters to create a “prefix”, and keep the rest as a “suffix”
4. This 5 character prefix is sent to the HIBP Pwned Passwords API
5. The API will return a list of 800-1000 “suffixes” of fully hashed passwords from data breaches that match the prefix we sent
6. Once we have received this list, we search these results for the presence of our original suffix and can then inform you whether the entered password has been part of a breach.
What should I do if the password I’ve used was in a breach?
Our first recommendation would be for you to change the entered password, and use something different. If you already use that same password elsewhere, we’d recommend you change it in those places as well, making sure you use a different password for every website.
We’d also recommend using a password manager to help remember all your passwords for you. on why password managers are beneficial in keeping your data safe and secure.
What’s next?
If we find that the feature works well, we could well integrate it further. We’re always looking to improve and would welcome feedback on this feature to help guide our future plans.
